Hardware Information Security

That s why apple devices running ios ipados macos watchos or tvos have security capabilities designed into silicon.
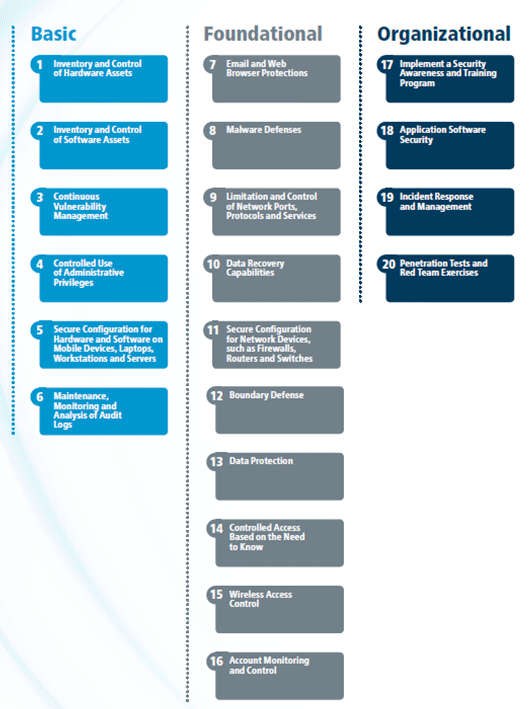
Hardware information security. Current efforts to provide electronic security largely rely on robust software development and integration. A principal benefit of the controls is that they prioritize and focus a smaller number of actions with high pay off results. As devices become connected and share real time information hardware security solutions will be required to enable autonomous real time decisions while maintaining resiliency in the factory. Present responses to hardware vulnerability.
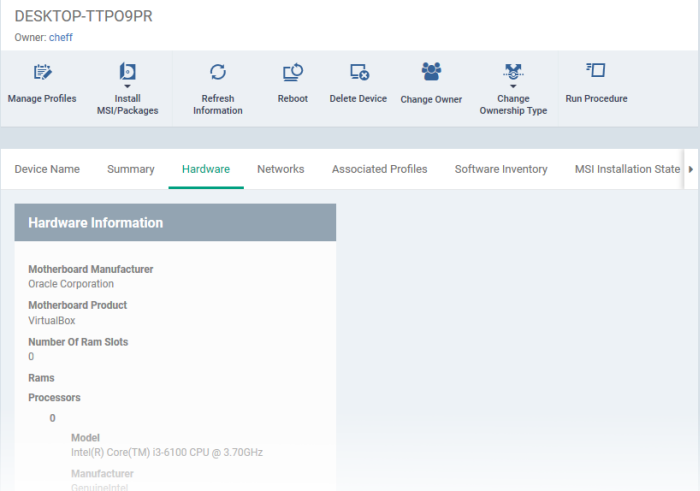
At the bottom of the device security screen one of the following messages appears indicating the security capability of your device. The cis critical security controls are a recommended set of actions for cyber defense that provide specific and actionable ways to stop today s most pervasive and dangerous attacks. A hardware vulnerability is an exploitable weakness in a computer system that enables attack through remote or physical access to system hardware. A hardware security module hsm is a physical computing device that safeguards and manages digital keys performs encryption and decryption functions for digital signatures strong authentication and other cryptographic functions.
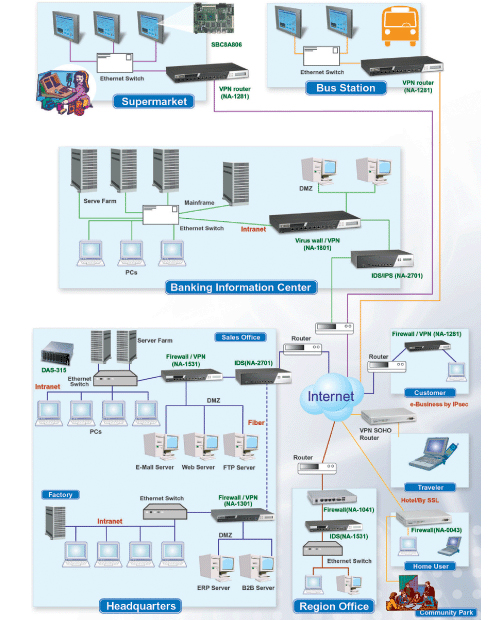
These include custom cpu capabilities that power system security features and silicon dedicated to security functions. Hardware authentication can be particularly important for the internet of things iot where a network wants to ensure that the thing trying to gain access to it is something that should have access to it. Electronic system security has become an increasingly critical area of concern for the dod and more broadly for security of the u s. Physical personal and organizational.
Any means by which code can be introduced to a computer is inherently a hardware vulnerability. Your device meets the requirements for standard hardware security. Secure software requires a foundation of security built into hardware. Tpm 2 0 also referred to as your security processor.
This means your device supports memory integrity and core isolation and also has. Information systems are composed in three main portions hardware software and communications with the purpose to help identify and apply information security industry standards as mechanisms of protection and prevention at three levels or layers.