Nessus Plugin Hardware Information

This section includes information and steps required for installing nessus and nessus agents on all supported operating systems.
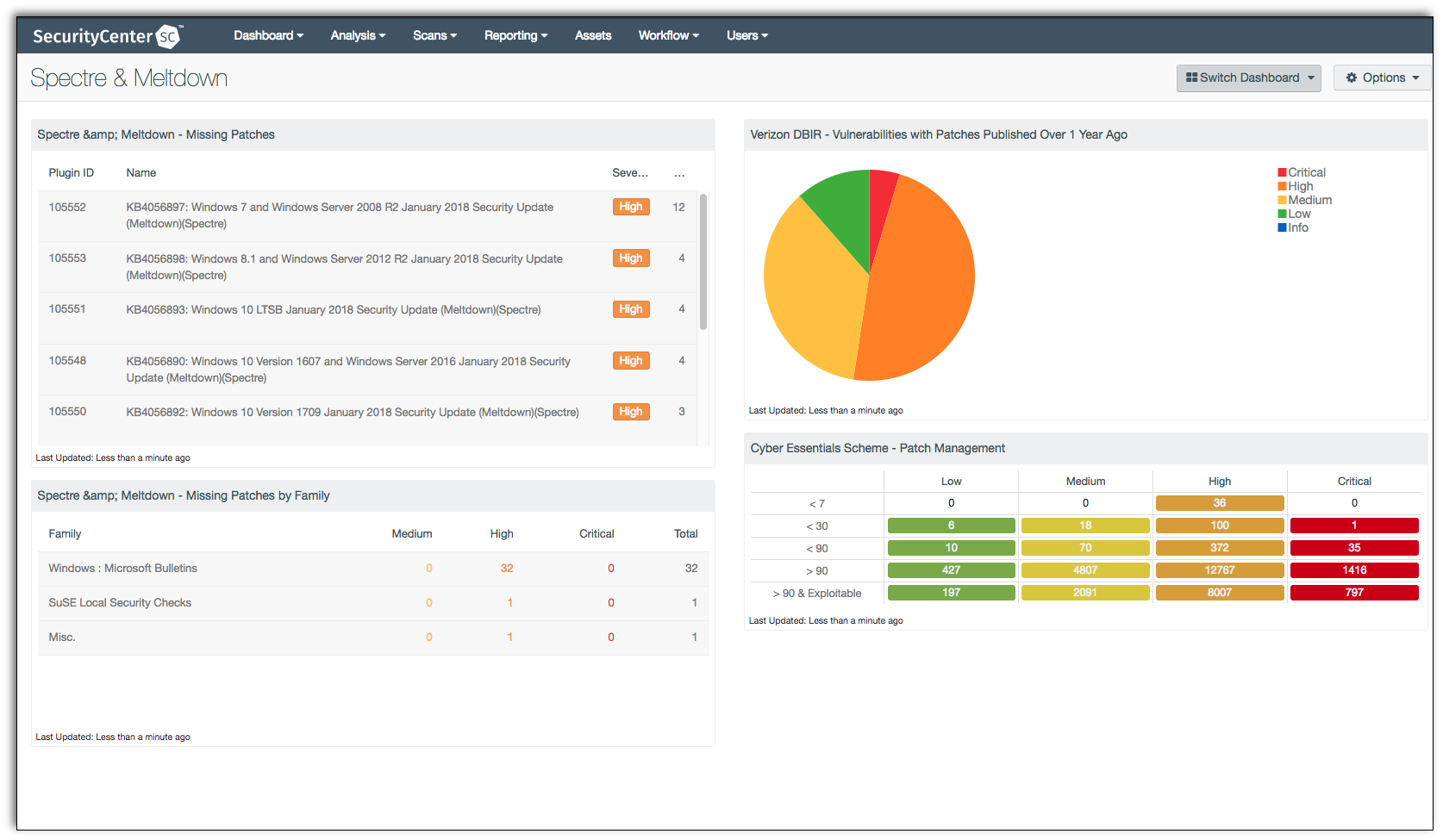
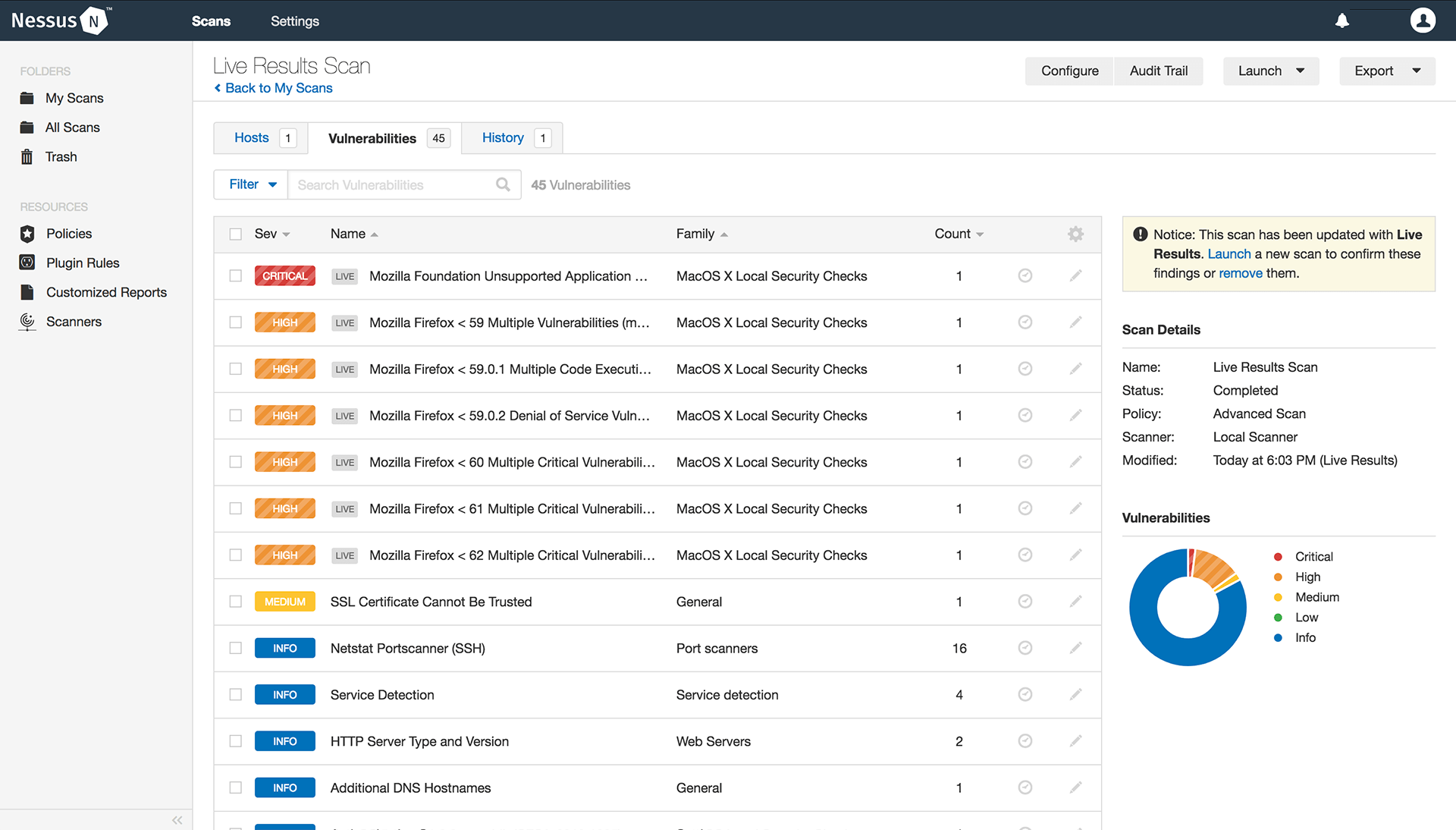
Nessus plugin hardware information. About nessus plugins as information about new vulnerabilities are discovered and released into the general public domain tenable inc. These programs are named plugins and are written in the nessus attack scripting language nasl. The version of the nessus engine. Tenable strongly discourages deploying tenable sc or tenable core tenable sc in an environment shared with other tenable applications.
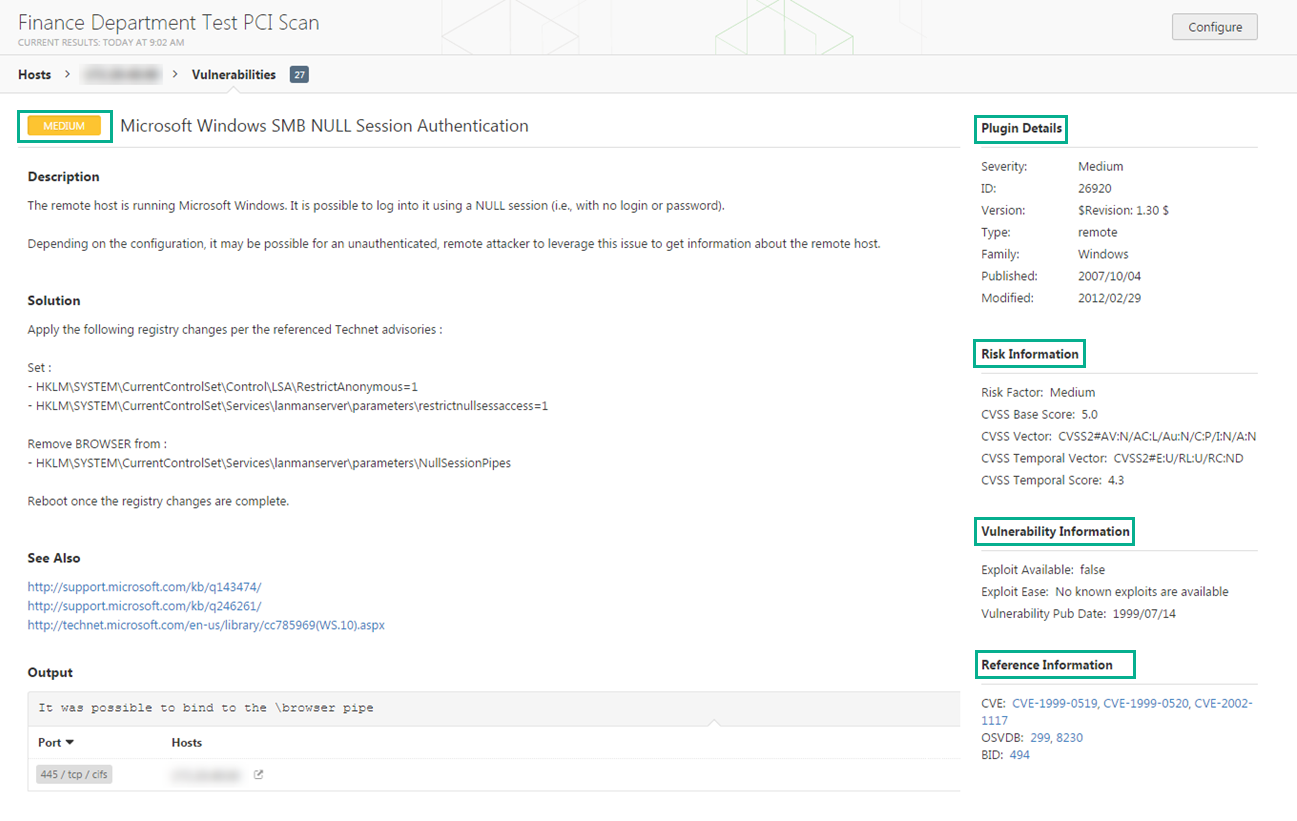
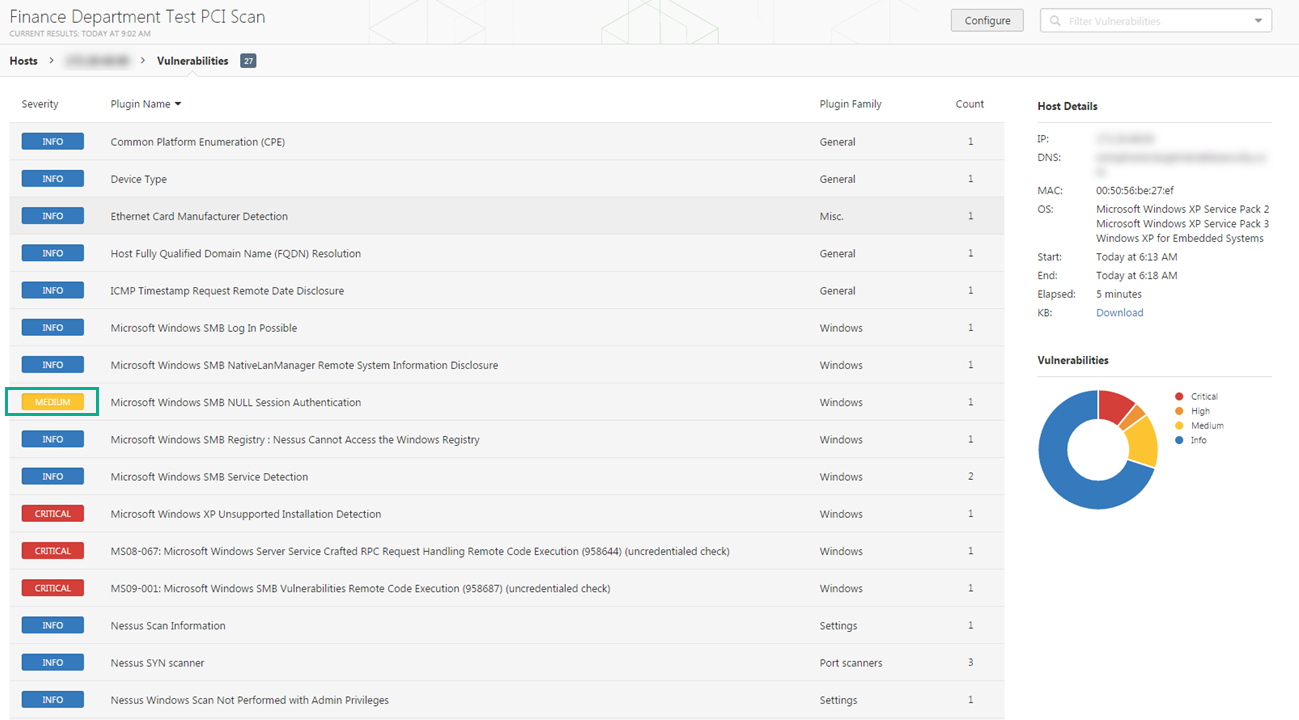
These programs are named plugins and are written in the nessus proprietary scripting language called nessus attack scripting language nasl. Description this plugin displays for each tested host information about the scan itself. The type of scanner nessus or nessus home. Note that if an official cpe is not available for the product this plugin computes the best possible cpe based on the information available from the scan.
Use the following hardware recommendations for tenable sc as a guide when preparing your physical or tenable core environment. The port range scanned. Nessus professional will help automate the vulnerability scanning process save time in your compliance cycles and allow you to engage your it team. Add advanced support for access to phone email community and chat support 24 hours a day 365 days a year.
The version of the plugin set. This plugin displays information about the nessus scan. Install nessus and nessus agents. The plugins contain vulnerability information a simplified set of remediation actions and the algorithm to test for the presence of the security issue.
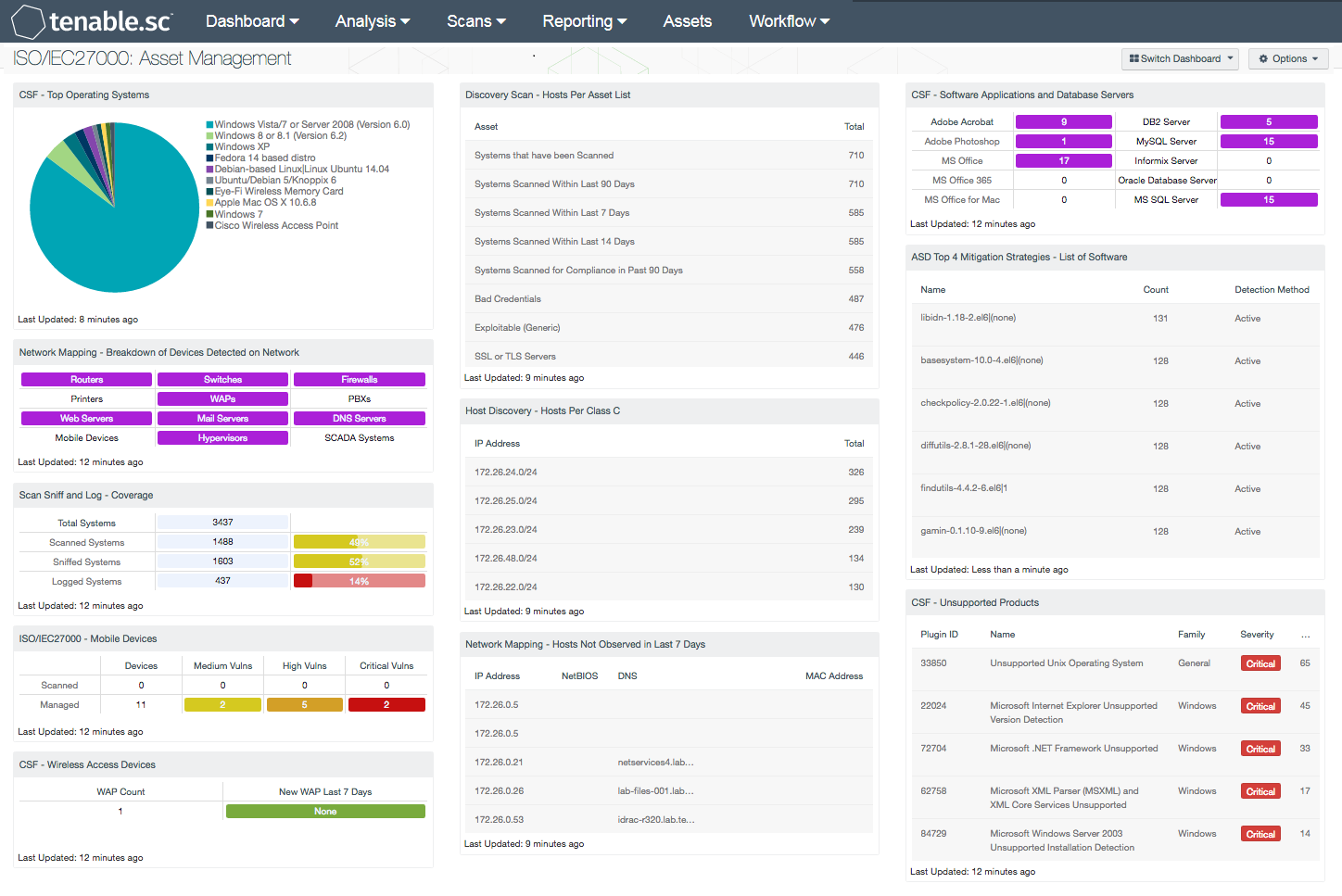
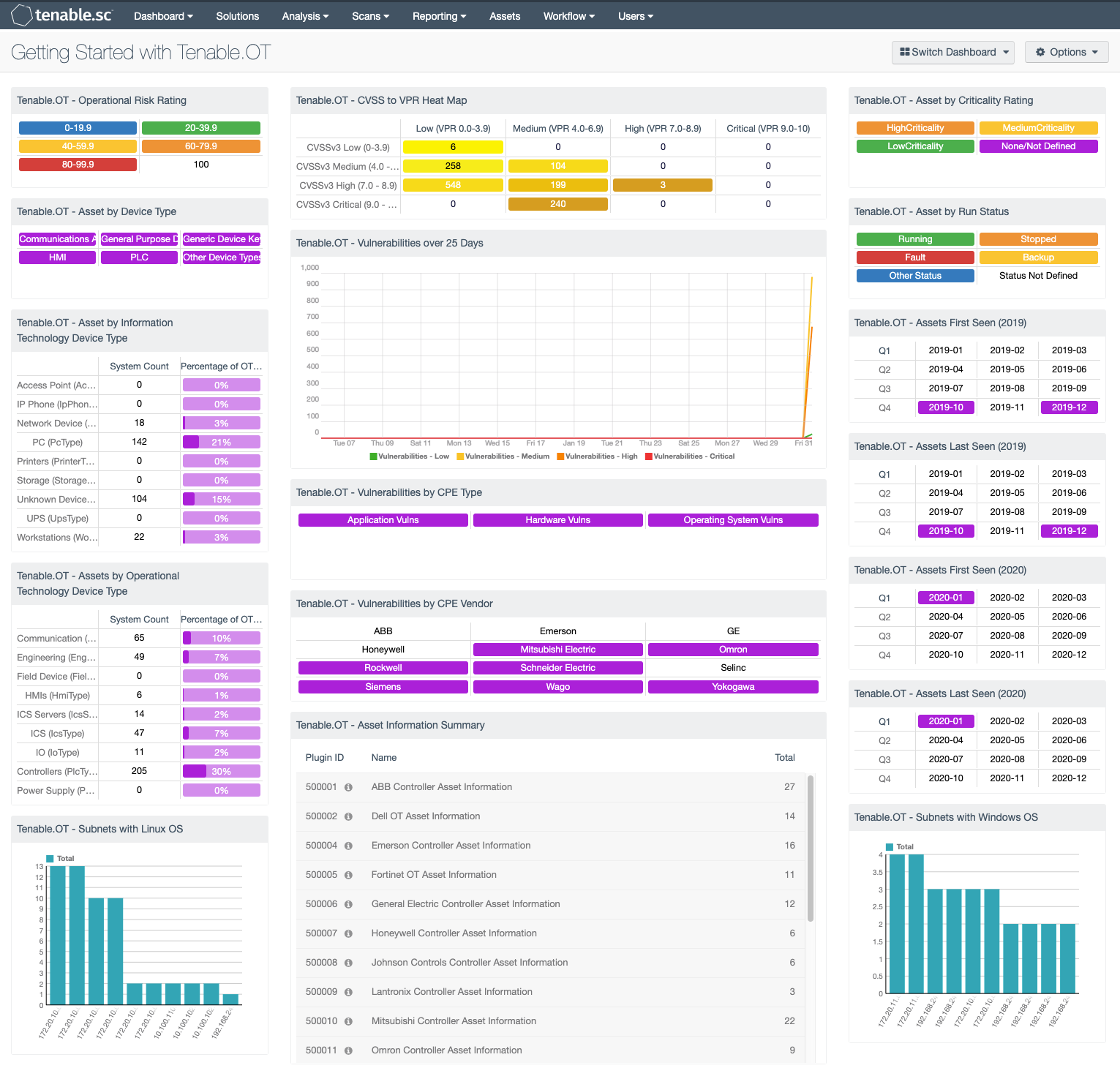
A nessus agent uses almost no cpu while idle but is designed to use up to 100 of cpu when available during jobs. Research staff designs programs to enable nessus to detect them. Tenable research has published 145060 plugins covering 57794 cve ids and 30691 bugtraq ids. Description by using information obtained from a nessus scan this plugin reports cpe common platform enumeration matches for various hardware and software products found on a host.
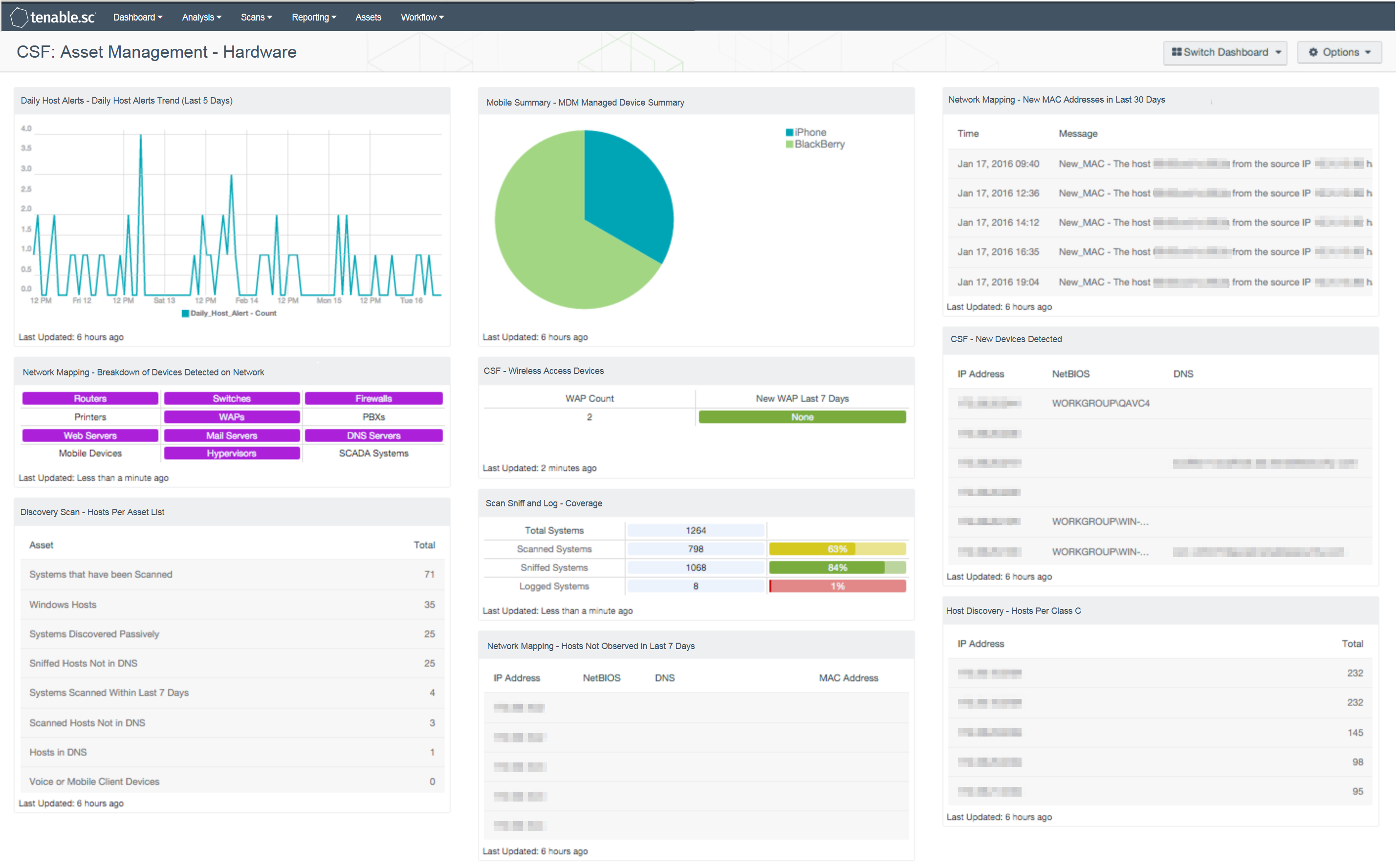
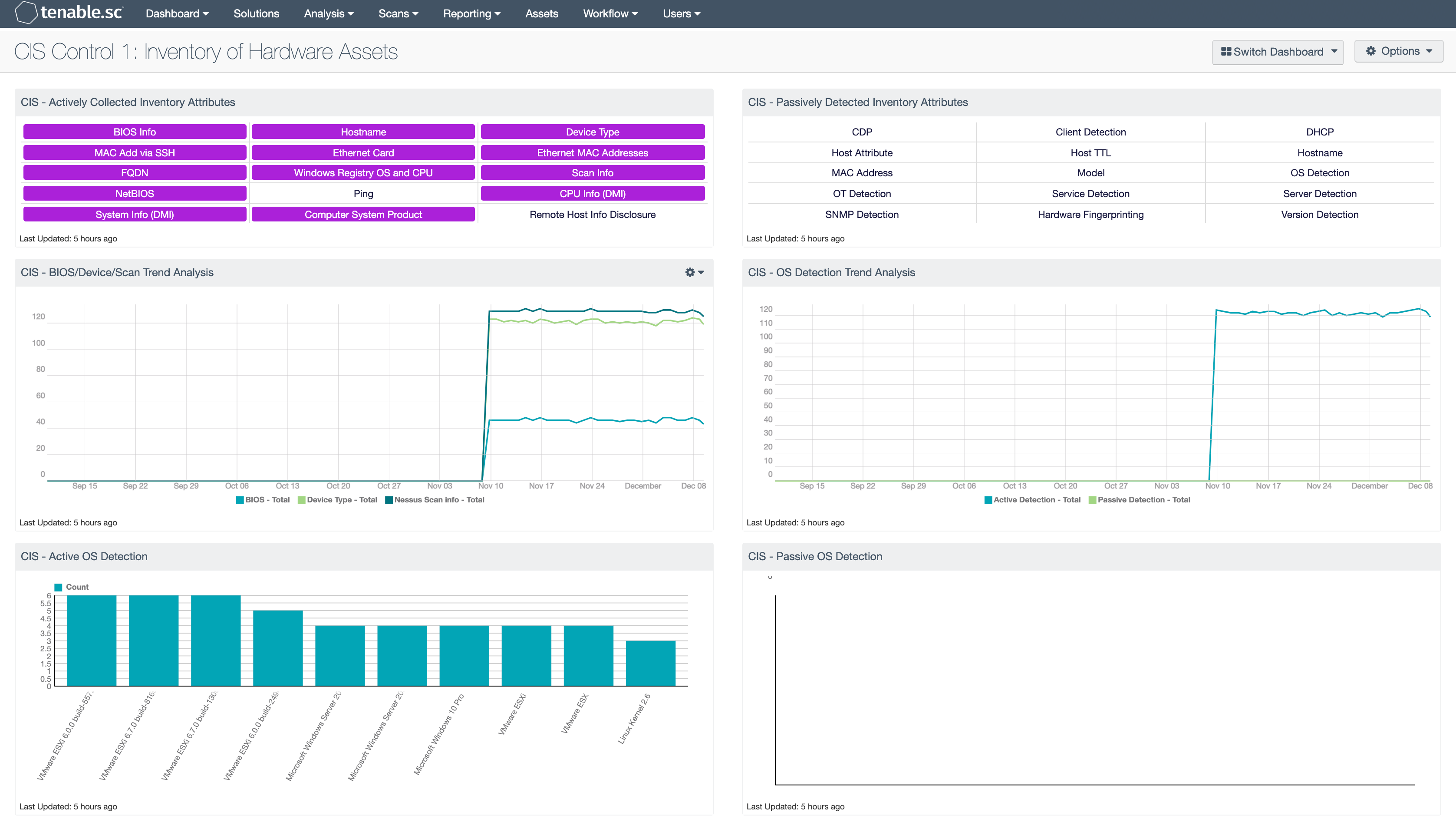
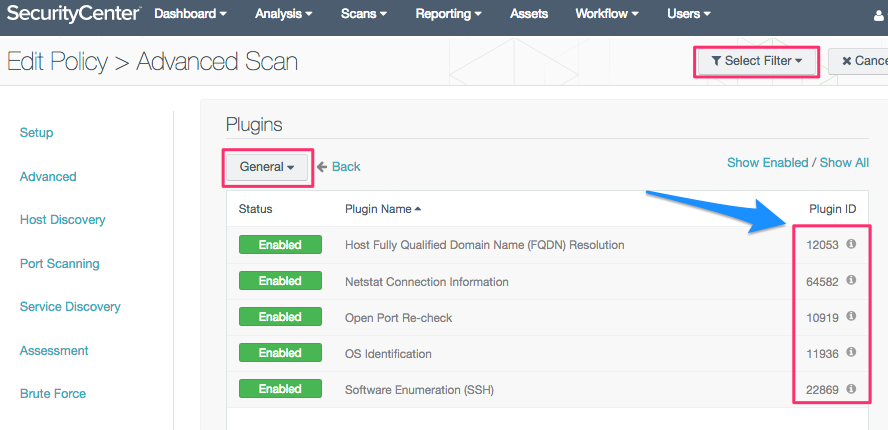
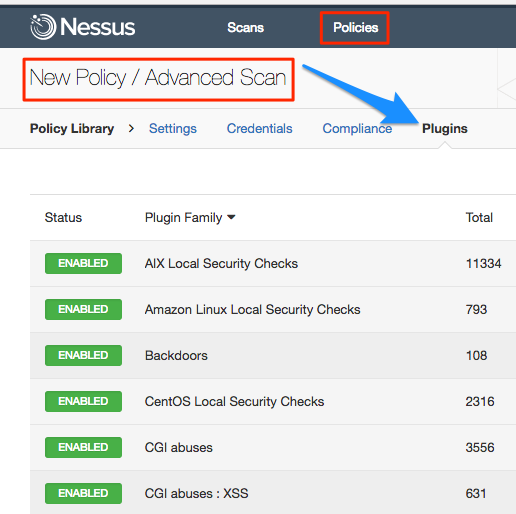
The following table summarizes the nessus plugin families. Buy a multi year license and save. Using the smbios aka dmi interface it was possible to retrieve information about the remote system s hardware such as its product name and serial number. Generally a nessus agent uses 40 mb of ram all pageable.
This allows a user to quickly enable or disable a large group of plugins that are relevant to the target being scanned or unnecessary for a given host. For more information see the announcement. Nessus plugin families nessus plugin families are designed to allow an efficient and accurate grouping of similar security checks.