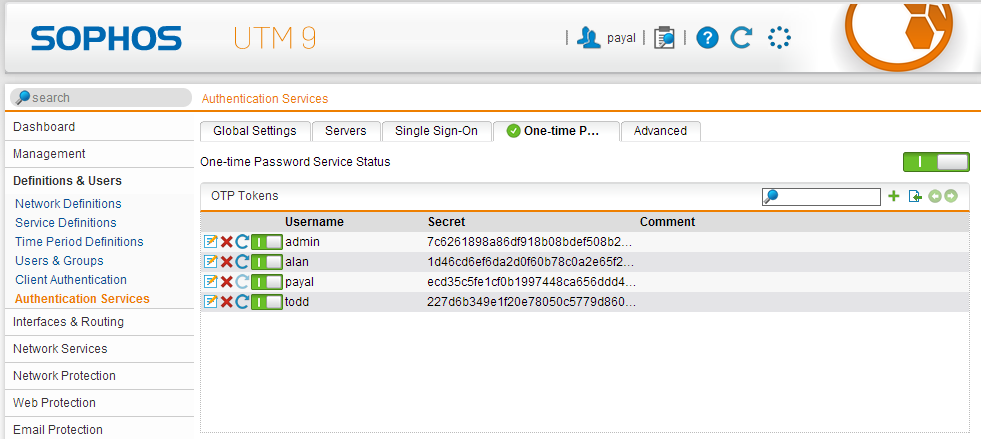
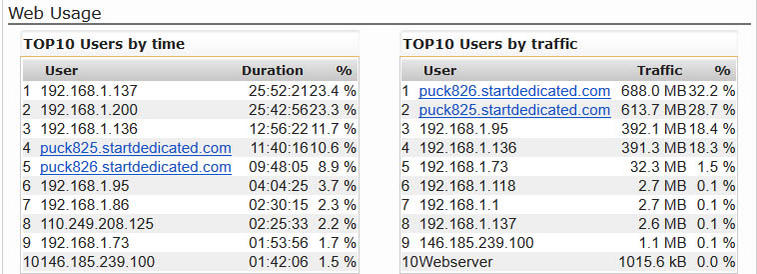
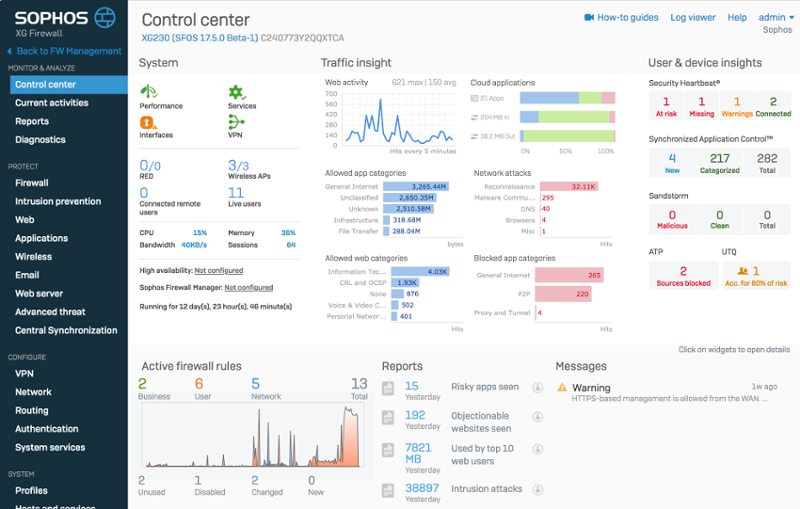
Sophos Firewall Hack

Sophos informed about the bug on april 22 2020 further analysis revealed that hackers can attack systems with either the administration interface https admin service or the user portal exposed on the wan zone.
Sophos firewall hack. Create a relevant https scanning exception and then enable http and https scanning in any relevant security policies. Zero day hack in sophos firewalls 2 summary. Navigate to hosts and services fqdn host. Sophos xg firewall hacked in the wild hotfix available sophos has rushed out a hotfix for its xg firewall products to close an sql injection vulnerability after hackers were spotted exploiting the hole in the wild.
Create https scanning exceptions. How to create firewall rules to bypass web proxy. Navigate to protect web exceptions and click add exception. Sophos patched a sql injection flaw with xg firewall product that exploited by attackers in the wild.
Sophos xg firewall vulnerability reportedly sophos has disclosed an sql vulnerability in its xg firewall that hackers actively exploited. Create a firewall rule for a website. How to bypass scanning. Add an fqdn host entry for the website.
Describing the details in an advisory sophos stated that they recently noticed an attack on xg devices which triggered them to investigate. Enter the parameters shown in the image below. To create a firewall rule to exclude a website from the web proxy. After initially downloading install sh to tmp and renamed to x sh on execution it.
Here are examples of different types of firewall rules that can be used to bypass the web proxy s scanning.