Sophos Firewall Hardening Checklist
Sophos central firewall management includes powerful cloud based group firewall management backup management one click firmware updates and rapid zero touch provisioning of new firewalls.
Sophos firewall hardening checklist. This checklist does not provide vendor specific security considerations but rather attempts to provide a generic listing of security considerations to be used when auditing a firewall only technical aspects of security are addressed in this checklist. Cloudera security hardening checklist. The leader in antivirus spam protection malware removal and network encryption. Endpoint protection with artificial intelligence.
The onion routing network research. Sophos utm firewall hardening. For over two decades public and private sector organisations across the world have relied on our. This checklist does not provide vendor specific security considerations but rather attempts to provide a generic listing of security considerations to be used when auditing a firewall.
Firewall checklist 1 0 pdf lead tbd. Free firewall sophos xg virtual firewall free for 90 days. Firewall network appliance craig simmons october 2000 introduction this checklist should be used to audit a firewall. Checklists step by step guides.
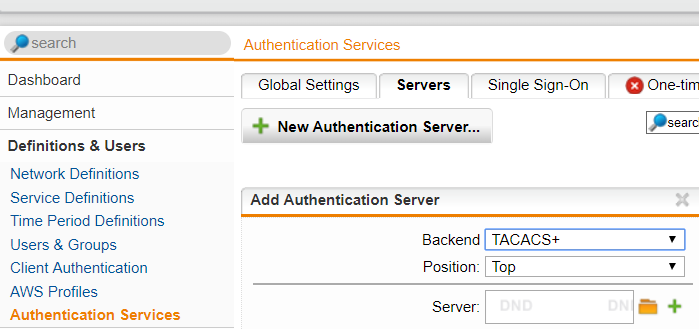
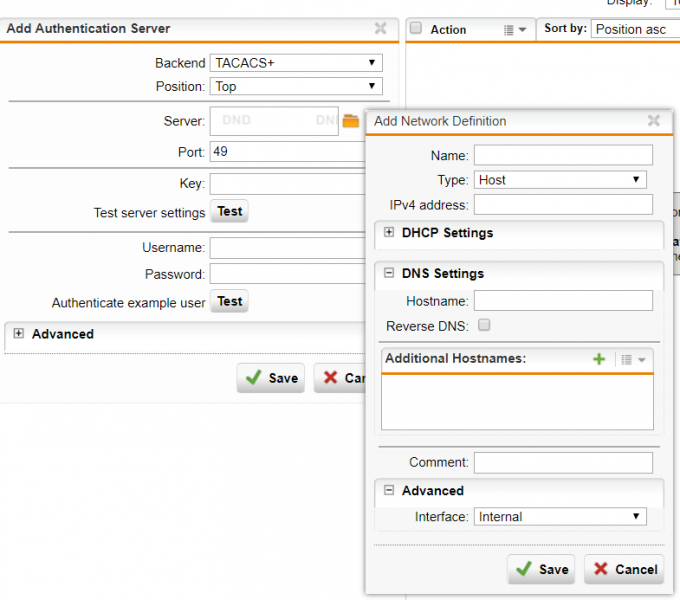
Sophos xg firewall sophos xg firewall provides comprehensive next generation firewall protection that exposes hidden risks blocks unknown threats and automatically responds to incidents. Sophos central firewall reporting provides flexible reporting in the cloud for all your xg firewalls with easy tools to create your own custom reports. This is a generic list and can be used to audit firewalls. The aim of this article is to provide guidance for network administrators on how to harden sophos utm firewalls.
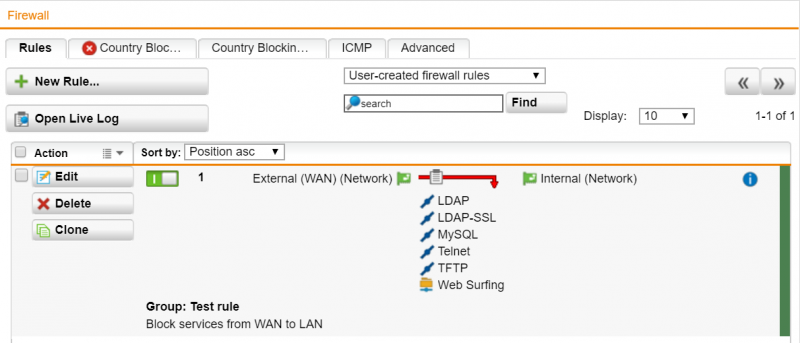
Dionach is an independent crest approved global provider of information security solutions with a wealth of globally recognised certifications including pci qsa pfi and iso 27001. Firewalls are used as the main defence for an organisation s network infrastructure and are used to prevent unauthorised access to or from the private network. The consolidation is done through personal experience as well as through research on various articles from the internet. Mac os x 1 0.
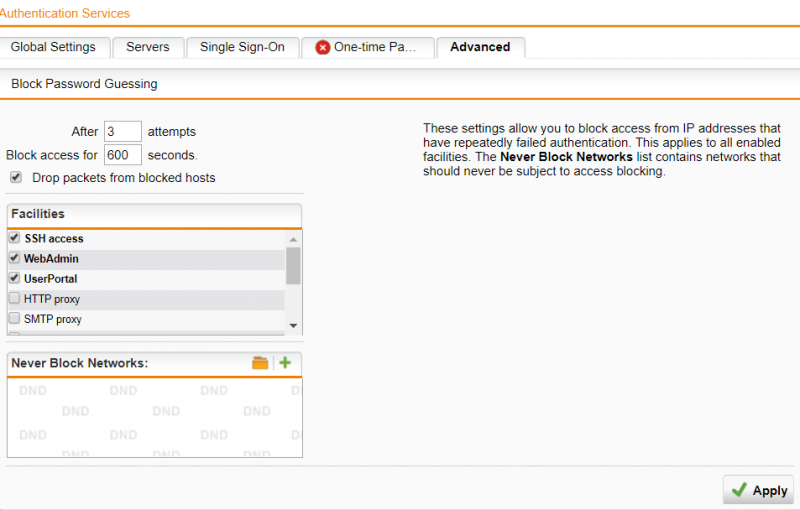
Sophos antivirus sophos firewall. Linksys broadband routers 1 0. The below mentioned are the best practices to be followed for firewall hardening. Malicious file investigation.
Firewall with synchronized security built in. Business 6 cyber security 29 cyber security news 338 design 11 email security 1 endpoint security 1. This checklist should be used to audit a firewall.