Sophos Firewall Rule 60001
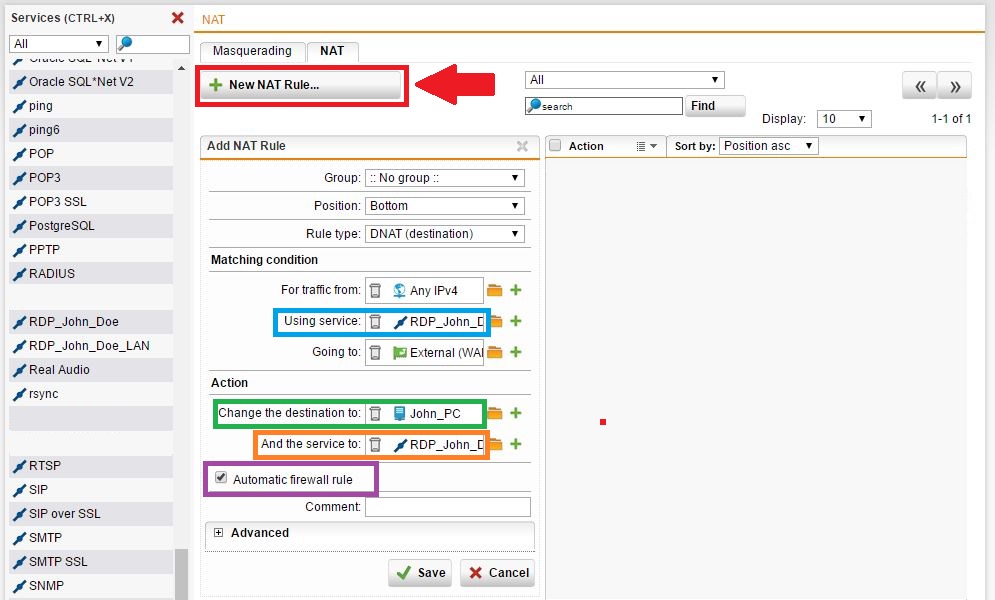
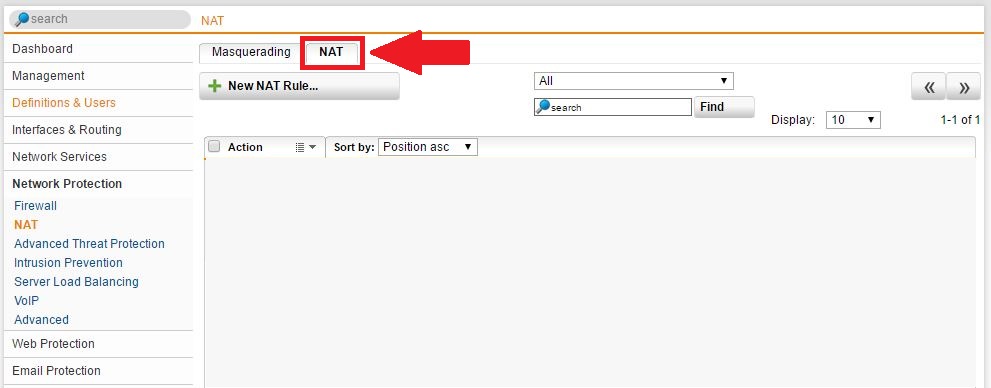
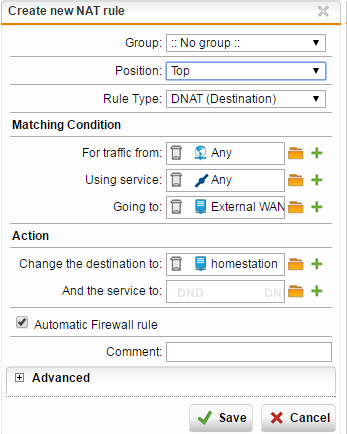
Most of the time fwrule 60001 means that you need to configure a nat rule likely dnat or review the configuration of your existing nat because the packet is not matching the intended rule.
Sophos firewall rule 60001. Check for interface binding that the source and destination port are correct that you are matching the correct procotol tcp udp both and that the ip addresses are correct. For information about the settings for the default global and application rules see sophos knowledgebase article 57757. Most of the time fwrule 60001 means that you need to configure a nat rule likely dnat or review the configuration of your existing nat because the packet is not matching the intended rule. Sophos central firewall management includes powerful cloud based group firewall management backup management one click firmware updates and rapid zero touch provisioning of new firewalls.
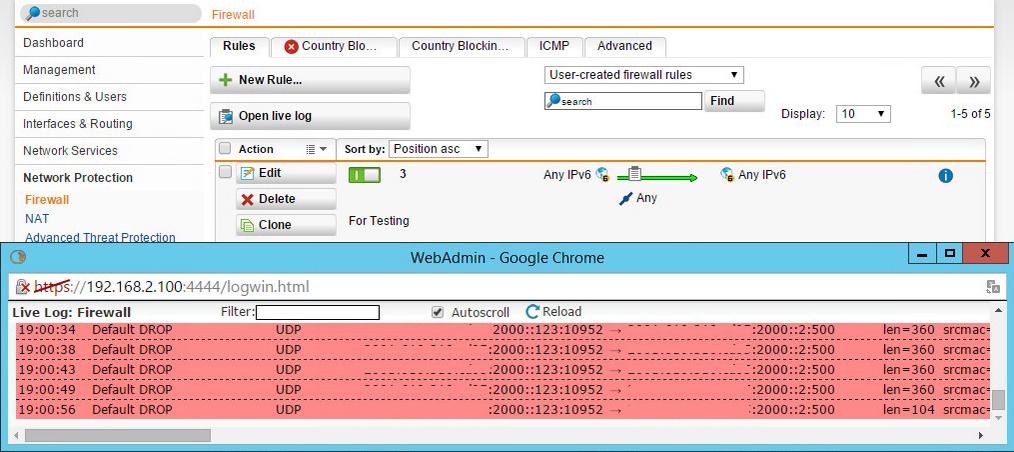
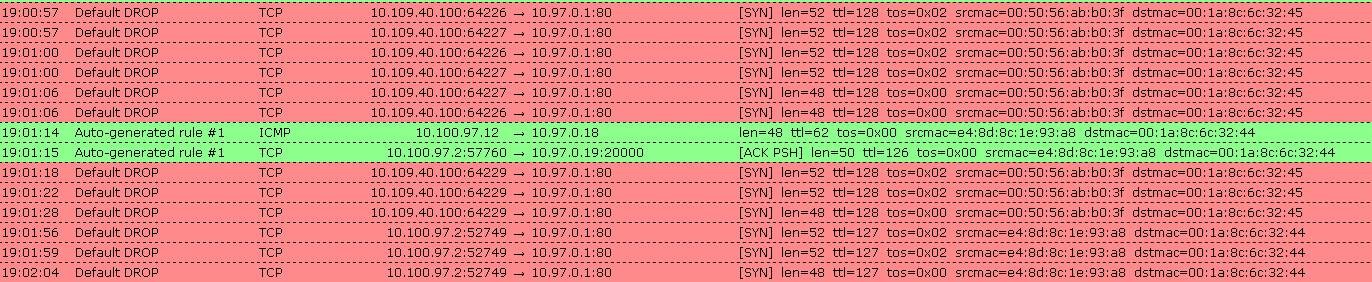
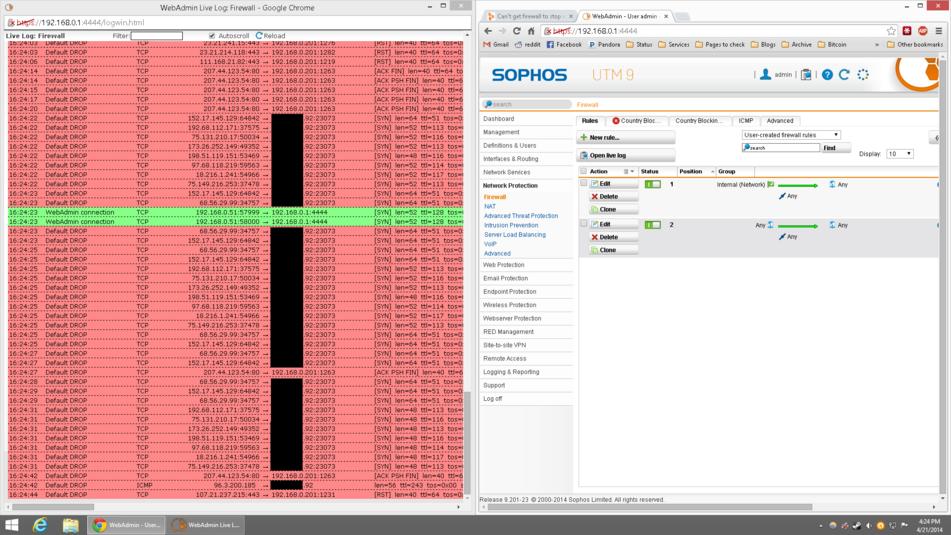
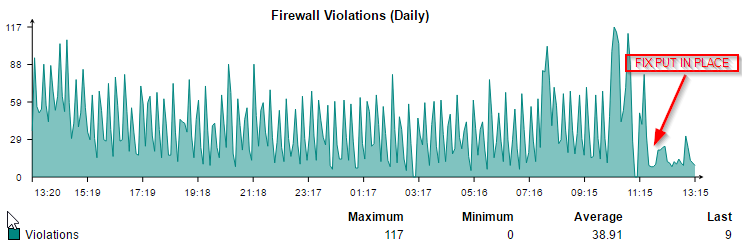
I haven t made any configuration changes. What used to be a very quiet fw is now very chatty with spikes of 60001 drops every 5 10 minutes. Note review rule positions after a firewall rule is created automatically or manually to make sure the intended rule matches traffic criteria. Also temporarily to conquer this issue.
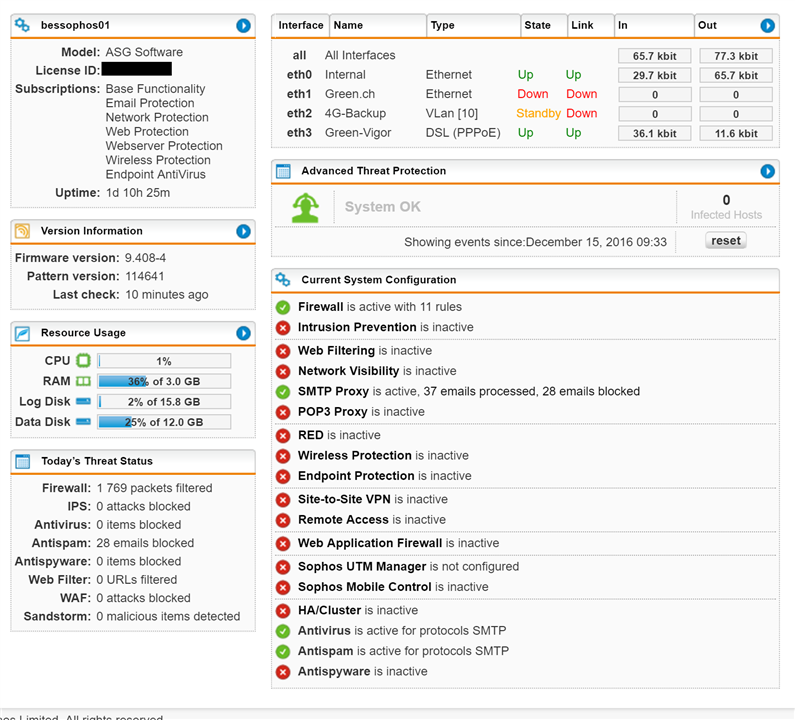
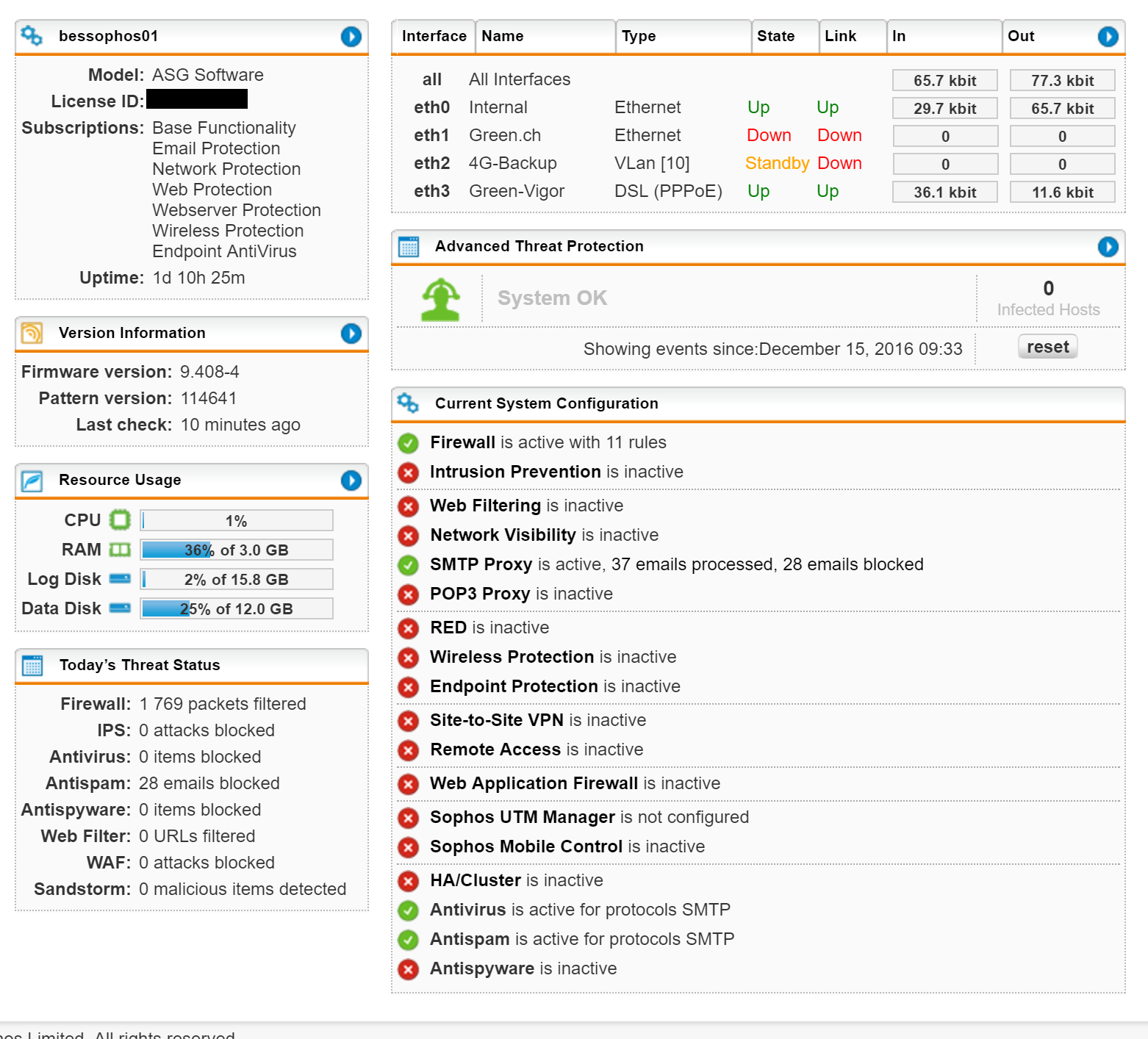
Our free home use xg firewall is a fully equipped software version of the sophos xg firewall available at no cost for home users no strings attached. In the firewall policy dialog box that appears click configure next to the location for which you want to configure the firewall. Only module left active is the firewall with a rule in place to allow everything from anywhere to anywhere. You can have one or more rules for an application.
All of a sudden i m seeing a lot of fw rule 60001 in the fw log. Sophos central firewall reporting provides flexible reporting in the cloud for all your xg firewalls with easy tools to create your own custom reports. You can either use preset rules created by sophos or create custom rules to give you fine control over the access allowed for an application. Firewall from the 200 lines of firewall log lines only 10 are not from rule 60001.
To create an application rule from a firewall policy. Automatically created firewall rules such as those for email mta ipsec connections and hotspots are placed at the top of the firewall rule list and are evaluated first. Double click the policy you want to change. We do not have any nat rules.
On the welcome page of the firewall policy wizard click the advanced firewall policy button.